As a Mac user, you’ve likely heard that macOS is renowned for its security. Yet, sometimes it’s easy to wonder – is your Mac really that secure? Is there something more you should be doing to maximize its defenses? You are not alone in having these concerns. We all want to feel confident that the sensitive personal or professional information on our devices remains safeguarded against evolving cyber threats.
The good news is your Mac comes equipped with a variety of built-in security tools to help with this, but it’s important to know what they are and how they work. By having a clearer understanding of these features, you’re not only protecting your Mac, but also gaining peace of mind. Below, we’ll walk through the core elements that macOS uses to keep your device secure and help you fend off potential dangers.
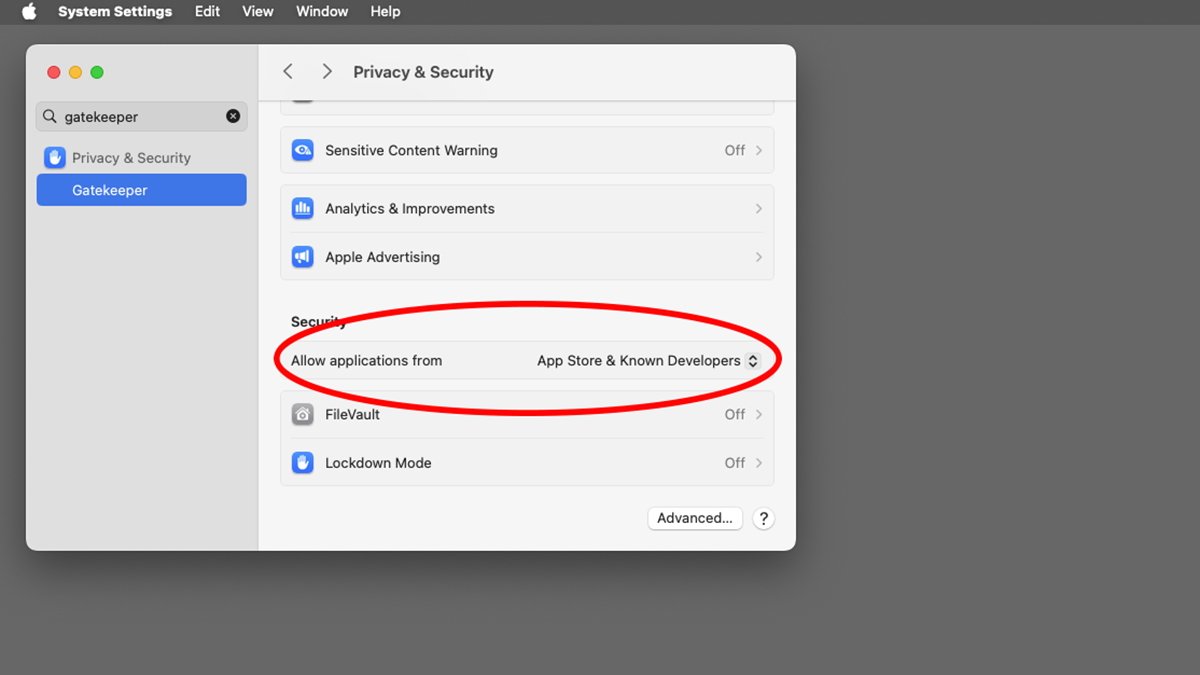
- Gatekeeper is one of macOS’s first lines of defense. Think of it as a security guard standing at the gates, inspecting every app you try to install. Gatekeeper ensures that apps either come from the Mac App Store or from verified, trusted developers. This cuts down the potential of downloading malicious software while still allowing you flexibility. Feeling uncertain about an alert that appears when installing something new? That’s Gatekeeper asking you if it’s safe to proceed. It adds an extra layer of protection, assuring you won’t accidentally run a risky app without a deliberate decision.
- XProtect adds another heartening layer to macOS security. It’s essentially a quiet guardian working in the background that you might never notice, but its impact is immense. XProtect functions similarly to an antivirus program, scanning downloaded files for known threats and stopping them in their tracks if something malicious is discovered. This means even if you happen to download dangerous software without realizing it, XProtect can prevent it from running, so you don’t have to deal with the consequences.
- FileVault protects your data in a different way. Have you ever worried about what would happen if your Mac was lost or stolen? FileVault encrypts your entire hard drive, making it impossible for someone to access your files without the right password. It’s so effective that even if someone physically has your device, they can’t get to your personal data without the correct credentials. If you’ve ever hesitated about enabling FileVault, think of it as locking your most precious information inside an unbreakable vault.
- System Integrity Protection (SIP) may sound technical, but here’s what you need to know: it makes sure nothing messes with important system files—items that keep macOS running smoothly and securely. By restricting even the root (admin) user’s ability to make critical changes, SIP ensures that malware or other malicious software can’t easily embed itself into your system where it can do serious damage.
- Sandboxing is like a protective, invisible bubble that surrounds every app you run on your Mac. Have you ever been cautious about downloading something but hoped it would remain isolated if things were to go wrong? Sandboxing does exactly that by isolating apps, limiting the resources they can access, and restricting their ability to interact with other programs or critical system areas. If one app acts up, it won’t be able to affect the rest of your system. You can relax knowing a rogue application is contained.
- Apple ID and Two-Factor Authentication also play crucial roles in macOS security. Your Apple ID ties everything together, from system settings to app usage, so securing this account is vital. Two-factor authentication goes the extra mile by ensuring that even if someone somehow learns your password, they’ll still need that second verification step (typically a code sent to your device) to access your account. If you’ve ever panicked about compromised passwords, enabling two-factor authentication helps alleviate those worries.
You don’t need to be a security expert to protect your Mac because, thankfully, many of these features quietly do their job in the background. Knowing they are there can help you feel more in control and deliberate in how you use and care for your Mac. Feeling reassured yet? Hang on to that sense of security, because there’s even more you can do. It’s important to stay proactive—and empowering yourself with knowledge of these features is a critical step in safeguarding the tech-forward world we live in.
Now that you’re familiar with the core security features of macOS, you might find yourself asking a crucial question: what can I do to make my Mac even safer? You’re not alone in this—every time we read about the latest cyber threats and data breaches in the news, it’s natural to feel a sense of unease. We work hard for our data—the personal photos we store, the sensitive financial records, the creative projects—and the good news is, there are plenty of proactive steps you can take to go the extra mile. After all, while your Mac is designed to be secure, adding layers of protection never hurts.
Below are some best practices that can help bolster your Mac’s defenses. Don’t worry if some seem too technical—they’re easier than you think and absolutely worth the effort. Plus, once they’re in place, they’ll give you lasting peace of mind. Let’s do this!
- Keep macOS Updated Regularly: This might seem basic, but we cannot stress enough how important it is to keep your macOS up to date. With each new release, Apple fixes bugs, patches software vulnerabilities, and enhances security features. Hackers love exploiting older versions, knowing that unpatched systems are more vulnerable. Set your Mac to download updates automatically by navigating to System Preferences > Software Update and enabling updates on autopilot. This ensures you won’t miss crucial security enhancements.
- Use Strong, Unique Passwords: We’ve heard this advice a million times, but honestly, it’s worth repeating. Using strong and unique passwords for your Mac and your Apple ID makes it exponentially harder for hackers to break in. Trouble remembering complex passwords? You’re certainly not alone there. That’s where a password manager can be a game-changer. Apps like 1Password or LastPass can safely store and generate complex credentials without you having to memorize them all. You deserve the peace of mind that comes from knowing your accounts are well-protected.
- Enable Your Firewall: Did you know that macOS comes with a built-in firewall? It’s not active by default, so this is one setting to turn on ASAP! Your firewall works by controlling the connections made to your Mac from the outside world, stopping unwanted or unauthorized traffic in its tracks. It can act as a valuable barrier, especially when you’re connected to public or shared networks. Head to System Preferences > Security & Privacy > Firewall and make sure it’s turned on. If you’re feeling a bit more advanced, you can also configure specific firewall options for more tailored security.
- Be Choosy About Your Downloads: It’s easy to get excited about a shiny new app or utility, but be mindful before hitting that “Download” button. Always favor the Mac App Store or the website of a trusted developer over random links promising auxiliary services. Remember Gatekeeper? It’s always watching, but it’s also important to use your own judgment and avoid anything that feels off. If something seems too good to be true, it probably is. Just trust your gut—and Gatekeeper!
- Keep Regular Backups Using Time Machine: Ever feel that little twinge of fear? You know the one—that sinking feeling that if something happens to your Mac, all your important files could disappear in an instant? Backups are your safety net. Time Machine, macOS’s built-in backup software, can automatically back up your data to an external drive. Just go to System Preferences > Time Machine, select a backup disk, and let it do the rest. In the worst-case scenario—maybe your Mac is stolen, or a ransomware attack strikes—you’ll be relieved to have your data safe and sound.
- Use a VPN (Virtual Private Network) When on Public Wi-Fi: Whenever you’re sipping on your latte at the local coffee shop and hopping on their unprotected public Wi-Fi, you’re at risk. Hackers can eavesdrop on unencrypted data sent over these networks. A VPN can help keep your privacy intact by encrypting your internet connection, making it nearly impossible for bad actors to snoop on your activities. Services like NordVPN or ExpressVPN are user-friendly and highly effective. It’s a small step that makes a big difference when you’re on the move.
- Regularly Review System & Application Privacy Settings: Take control of who and what is accessing your data by reviewing your privacy settings periodically. Go to System Preferences > Security & Privacy > Privacy, and you’ll see a list of apps and services that currently have access to your camera, microphone, location, and other sensitive areas of your Mac. If any of them seem unnecessary, revoke their permissions. It’s your data—keep it as private or as open as you see fit.
- Monitor Your Mac’s Health with Activity Monitor: If you ever feel like your Mac is running slower than usual, or something feels off, Activity Monitor is there to help. It provides insight into what’s running on your system—whether it’s apps, processes, or resources you weren’t aware of—and lets you spot anything unusual. Open up Activity Monitor from your Applications > Utilities folder, and check for any unrecognized processes. If something seems suspicious, it might be worth investigating further.
- Learn to Spot Phishing Scams: We’ve all received those suspicious emails, and sometimes, they’re all too convincing. Phishing scams—where attackers pretend to be trusted entities to get you to give up sensitive information—are getting more sophisticated. The best defense? Be skeptical. Before clicking on links within an email, hover over the link to see if it leads to where it claims. If you’re in doubt, visit the website directly through your browser rather than clicking on links in an email. With phishing, a little bit of caution goes a long way.
Implementing these best practices doesn’t require hours of your time or special technical know-how, and the payoff is huge. Protecting your Mac from threats is a combination of leveraging its built-in strengths and adopting habits that extend its security. You’re not just investing in your computer’s safety, but you’re also preserving your peace of mind, knowing that you’re actively guarding your valuable data. Every step you take brings you closer to feeling fully secure in knowing that your Mac—and the personal information stored on it—are as safe as they can be.
It’s easy to think that because you’re using a Mac, you’re automatically safe from malicious attacks. After all, Apple has a well-earned reputation for building secure software and hardware. However, as the old saying goes, there’s no such thing as being “too careful,” especially in the digital world. Increasingly, hackers are targeting macOS users with sophisticated malware designed to take advantage of even the smallest vulnerability. It’s not just something that happens to “other people.” Understanding the types of malware that target macOS can greatly help you stay one step ahead of potential threats.
If you’re feeling uneasy about what might be lurking unnoticed in your system, don’t worry—you’re not alone in feeling this way. It can be hard to tell what’s out there if you’re not sure what to look for, but knowledge is your best defense. Here’s a closer look at the types of malware specifically designed to affect macOS systems, so you can recognize the risks and take action to safeguard your data.
- Adware: This type of malware comes disguised as seemingly harmless software, but once installed, it bombards your Mac with relentless advertisements. These intrusive ads may pop up in your browser or elsewhere on your system. The ads themselves can be annoying, but the real danger lies in the fact that some of them may lead you to malicious websites designed to steal your data. The frustrating part? Adware often finds its way onto systems through seemingly legitimate downloads, catching even the most cautious users off guard. If you’ve been seeing an unusual number of ads lately, adware could be the culprit.
- Spyware: It sounds like something from a movie, but spyware is a real and growing threat for macOS users. Spyware is designed to secretly track everything you do on your Mac—your keystrokes, browsing habits, passwords, and even personal conversations. This malicious software often operates quietly, collecting valuable data without you ever realizing it’s there. If you’re noticing odd system behavior like a sudden slowdown or strange network activity, spyware may be at play. The thought of someone watching your every move is unsettling, but being aware of this type of attack can help you spot the warning signs.
- Trojan Horses: Just like the infamous story from ancient Greece, Trojans on your Mac hide in plain sight, disguised as useful or legitimate applications. Unfortunately, once these “Trojan horses” are downloaded and executed, they allow malicious actors to take control of your system, giving them unfettered access to your files, personal data, or even your webcam. Trojans don’t always wreak havoc immediately, which makes them even more insidious—they might operate in the background unseen for weeks or months before they strike. If you’ve downloaded a mysterious app or noticed settings being changed without your permission, a Trojan could be responsible.
- Ransomware: Imagine booting up your Mac one morning only to find you’re locked out and greeted by a message demanding money to regain access to your files. That’s exactly what ransomware does. This particularly harmful type of malware encrypts your data, holding it hostage until you pay the hacker’s ransom demand in hopes of getting your files back. In many cases, even after paying, the data remains encrypted—and the loss of critical personal or professional information can be devastating. The best defense against ransomware is preparation; regular backups are key to making sure you can recover your data without paying a cent.
- Cryptojacking (or Cryptomining): As cryptocurrencies gain popularity, malicious actors have found ways to hijack the processing power of unsuspecting users’ devices to mine digital currencies. This is called cryptojacking. It essentially turns your Mac into a digital worker bee, constantly performing complex calculations in the background, which can slow down your system and cause overheating. Even more troubling, cryptomining malware can easily go unnoticed, steadily draining your resources and putting your hardware at risk. If your Mac suddenly starts running slower than normal or your fan is running all the time despite minimal activity, cryptojacking malware might be at fault.
- Keyloggers: A keylogger’s primary goal is to record everything you type on your keyboard. That means passwords, credit card details, personal messages—it’s all up for grabs. Once this information is logged, it’s transmitted back to the hacker who can use it for identity theft, financial fraud, or even corporate espionage. Keyloggers can be particularly terrifying because they are so hard to detect and, if left unchecked, can expose large amounts of sensitive information over time. Frequent monitoring and the use of anti-malware software can help detect keyloggers before they cause too much damage.
- Macro Viruses: While you may think that macro viruses are most associated with Windows computers, macOS isn’t immune. These viruses disguise themselves as innocent macro scripts in document files (such as Word or Excel), but once opened, they execute malicious commands in the background. They can attach themselves to other documents and quickly propagate across your system or even to other computers you share files with. If you regularly work with document downloads and suddenly notice strange behavior in those files, it’s worth investigating whether a macro virus is involved.
It’s natural to feel uncomfortable upon learning about these threats, especially if this is your first time confronting the types of malware that exist. But remember—you don’t need to feel helpless! macOS has robust layers of security already in place, and with a little bit of extra vigilance, you can actively reduce the chances of falling victim to these types of attacks. By staying aware of the warning signs and taking simple actions (like regular scans, cautious downloads, and keeping your software updated), your Mac is far more likely to stay malware-free.
Above all, stay calm, stay informed, and be proactive—your Mac’s safety is well within your control!
Now that you’re aware of the types of malware that can target your Mac, it’s natural to wonder what additional steps you can take beyond the core macOS security features. Thankfully, there are several tools and settings you can utilize to enhance your protection even further. By taking a few proactive steps, you’ll not only reinforce your defenses but also build an extra sense of security. Let’s explore some key tools and settings that can give your Mac the additional protection it deserves.
- Third-Party Antivirus Software: While macOS has built-in security features like XProtect and Gatekeeper, adding a reputable antivirus program can provide more thorough, real-time scanning for malware, ransomware, and phishing attacks. Programs like Bitdefender, Malwarebytes, and Sophos are popular choices that work in tandem with macOS security features while offering additional layers of protection. These tools scan your system for threats not only when files are downloaded but continuously in the background, helping to ensure that new and evolving threats are caught early.
- Malicious Website Protection: Many antivirus solutions offer browser extensions that can block you from visiting malicious websites. These extensions alert you when you’re about to enter a potentially dangerous site, helping to prevent phishing attempts and rogue downloads. If downloading antivirus software feels like overkill, you can set your browser to block pop-ups and suspicious websites manually via the privacy settings. Browsers like Safari, Chrome, and Firefox all offer strong protection options to prevent web-based threats.
- Turn On Advanced Firewall Options: The built-in macOS firewall is robust, but it becomes even more effective when tailored to your specific needs. By going to System Preferences > Security & Privacy > Firewall > Firewall Options, you can enable “Stealth Mode.” Stealth Mode makes your Mac invisible to external scans from hackers by preventing responses to probing requests from unwanted traffic, effectively making it harder for outside entities to know your Mac is even on the network.
- Use an IDS/IPS System: If you’re tech-savvy or just eager to learn, consider setting up an Intrusion Detection System (IDS) or Intrusion Prevention System (IPS). These systems monitor your network for suspicious activity, such as unauthorized access attempts or abnormal data transfers, and alert you to potential threats before they escalate. Tools like Snort or Suricata are open-source platforms that can complement your home network’s firewall, providing another layer of vigilance in detecting abnormal behavior.
- Security Audits with Objective-See: Objective-See offers a suite of free, macOS-specific security tools that can help you audit how secure your system really is. For example, “Lulu” is a free, open-source firewall that lets you monitor and block outgoing network connections from apps. You might be surprised by some of the apps attempting to reach out to the internet without your knowledge! The “BlockBlock” tool alerts you to persistent software trying to install itself upon rebooting your Mac. Use these tools not as a replacement, but as a complement to macOS security features to help tighten up your potential vulnerabilities.
- Maintain a Regular Backup Strategy: We discussed using Time Machine earlier, but it’s also worth considering having a redundant external backup plan. In addition to Time Machine, tools like Carbon Copy Cloner or SuperDuper! can create full, bootable duplicates of your Mac’s hard drive. In the unfortunate event of a ransomware attack or critical hardware failure, having multiple backups is invaluable and ensures that your important data is recoverable even if one backup method fails. Avoid cloud-only backups when sensitive data is concerned—offline backups are less vulnerable to remote attacks.
- Advanced Malware Detection: For those who want to leave absolutely nothing to chance, consider installing malware detection software designed specifically to recognize threats targeting macOS. Tools like KnockKnock and VirusTotal can scan for persistent malware and unwanted background programs. These tools often scan for startup items, plug-ins, login items, and other potentially malicious software that traditional antivirus apps might miss.
- Enable Encryption for External Drives: If you’re diligent about using external drives for backups or transferring sensitive information, make sure to encrypt them as well. macOS offers built-in encryption options that are easy to enable. Right-click (or Control-click) on the external drive in the Finder, then choose “Encrypt” from the options. This small step can prevent your data from being accessed even if your external drive falls into the wrong hands.
- Review Your Sharing Preferences: Under System Preferences > Sharing, you’ll find various services that allow your Mac to share files, printers, and other resources with other devices on your network. Make reviewing these settings a regular habit. Turn off any services you don’t use (like File Sharing, Remote Login, or Remote Management), as these services can leave your machine open to unwanted network connections.
Taking these steps now—before any incident happens—puts you in the driver’s seat when it comes to your security. Yes, macOS provides a solid baseline of protection out of the box, but many of the tools we’ve covered can give you the extra assurance you deserve. Hackers are opportunistic— they thrive on gaps in security, so the more you close those gaps, the less likely you are to fall prey to their game.
You’re not just following security best practices here—you’re claiming your digital peace of mind, one simple action at a time. So, go ahead—empower yourself by implementing these tools and settings today and rest easy knowing your Mac is insulated against even the most cunning of cyber threats.
