Booting from an external drive offers incredible convenience—it allows you to run macOS or other operating systems while keeping your internal drive untouched. Whether you’re a developer seeking a test environment, a creative working with large external drives, or just someone looking to maintain an alternate macOS setup, it’s no wonder this feature is a favorite. But then you encounter an unexpected roadblock: Apple Intelligence, one of macOS’s most powerful features, is disabled when using an external drive as your Startup Disk. Frustrating, right? Let’s take a closer look at why this happens and how macOS approaches this restriction.
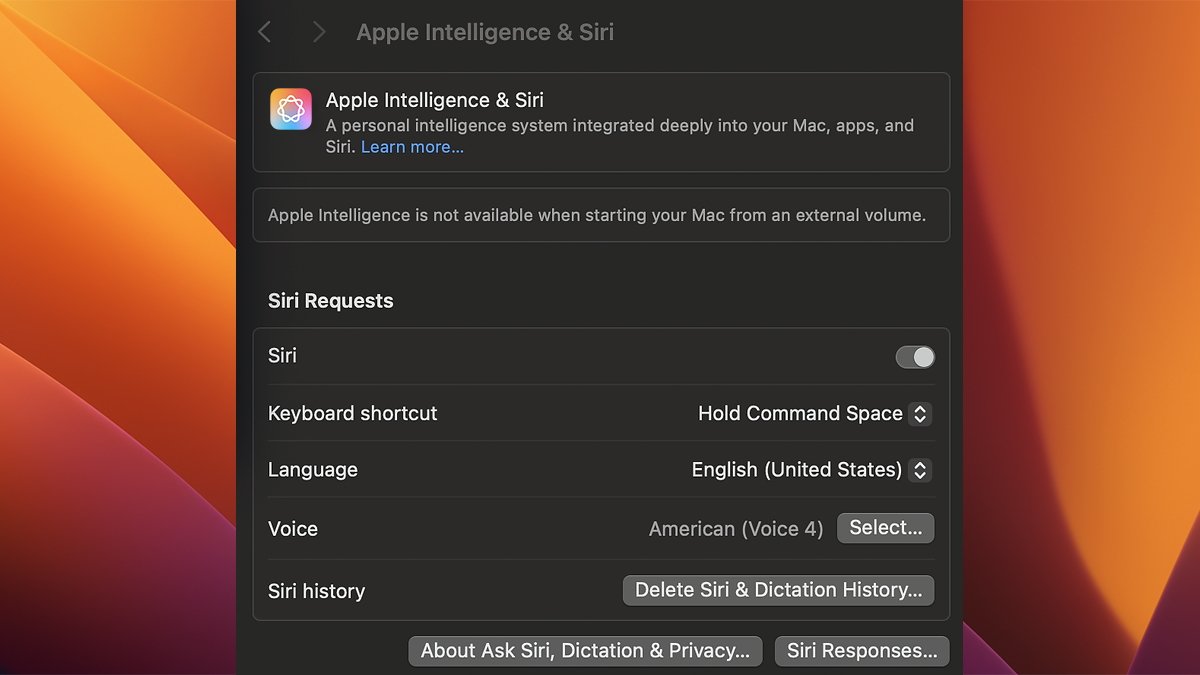
First, let’s address the elephant in the room: Apple Intelligence is designed to make your Mac experience smarter, faster, and more intuitive. It powers advanced features like natural language Siri functionality, proactive suggestions, and contextual awareness. When you boot macOS from your external drive, the lack of Apple Intelligence can feel limiting. But Apple has its reasons—strong ones rooted in security and performance concerns.
Security is the primary factor. External drives are naturally more portable and, therefore, more vulnerable. Imagine plugging your portable SSD into another machine, or leaving it connected to an unattended workstation. This opens a Pandora’s box of potential risks—malware lurking in shared networks, unauthorized tampering, or the inadvertent exposure of sensitive machine data. By disabling Apple Intelligence, which relies on intricate data handling, Apple ensures that these risks are minimized. It’s like locking a vault inside a fortress when you’re stepping out with the key.
Another critical consideration is system performance. Apple Intelligence operates using significant resources, integrating tightly with macOS’s localized neural engines and hardware optimizations. While this works seamlessly on an internal drive with direct access to your Mac’s ultra-fast storage and connections, things slow down when external drives are involved. This is particularly true for USB-connected drives, where the data transfer speeds are far slower than Apple’s high-bandwidth Thunderbolt standard. The last thing you want is a sluggish experience while trying to enjoy the flexibility of an external boot setup.
There’s also the matter of ensuring global compliance. Apple continuously tailors the availability of its services based on regional regulations and feature requirements. For example, Apple Intelligence itself isn’t yet available in certain countries, including parts of the EU and China. Similarly, features such as Apple Pay are also disabled when booting from external drives. These limitations add another layer to the decision-making process when aligning Apple Intelligence with external boot setups.
At its core, macOS relies on a built-in process known as eligibilityd, which assesses a long list of factors to determine what features are permissible. This system analyzes inputs like location, language, country code, and yes, even whether you’re booting from an internal or external drive. The result is a highly curated feature set designed to operate securely and efficiently, but which, unfortunately, limits functionality for external drives by default.
It’s absolutely understandable to feel a mix of frustration and confusion when you realize these features are disabled, especially if you depend on them in your workflow. This limitation might even feel like a step backward for those who love the versatility of external drives. But understanding the “why” behind these restrictions is the first step toward finding solutions and workarounds to fit your specific needs. Once you fully grasp the reasoning, you’ll find it’s less about Apple trying to hinder your flexibility and more about protecting you and ensuring top-tier performance.
Now that you know the rationale behind Apple disabling Apple Intelligence on external boot drives, let’s explore how to modify eligibility settings to regain the functionality you need. While Apple’s default implementation is designed with caution in mind, advanced users have discovered workarounds—some simple, others requiring a bit more technical finesse. By carefully editing macOS’s hidden system files, you can modify settings to enable Apple Intelligence without compromising performance or security, so long as these steps are executed with precision.
The first step begins with a fundamental understanding of macOS’s eligibility system. As previously highlighted, a process called eligibilityd controls feature permissions on your Mac. It decides whether certain services like Apple Intelligence or even Apple Pay should be active based on various contextual parameters. These include verification of whether macOS is running from an internal drive or an external one. These parameters are stored and referenced in files located deep within macOS’s system folders, specifically at /private/var/db/eligibilityd.
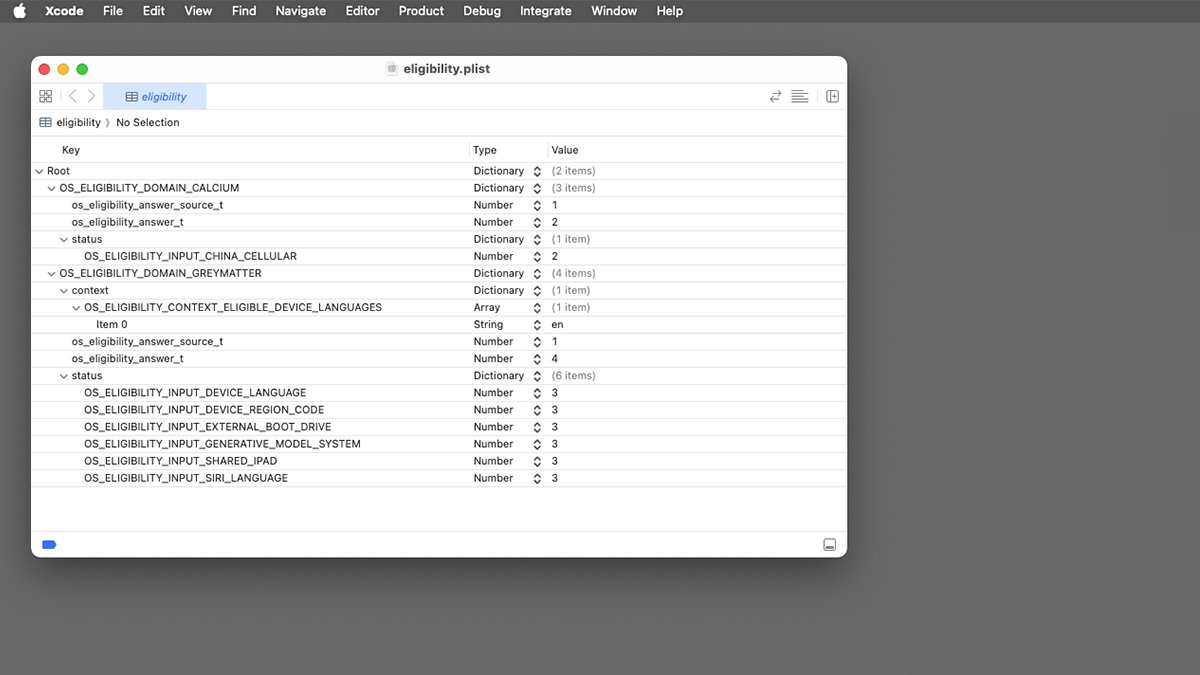
Inside this folder, you will find three important files: domains.data, eligibility_inputs.plist, and eligibility.plist. These files essentially define the rules and logic that determine which macOS features are accessible. To regain Apple Intelligence functionality when booting from an external drive, minor adjustments to these files can override the default restrictions. Here’s how to proceed:
-
Enabling Hidden Files in Finder: Since these critical files are located in a hidden system directory, you’ll need to make hidden files visible in Finder. Press
Command + Shift + .(period) in Finder to toggle visibility of hidden files. -
Locating the Eligibility Files: Navigate to
/private/var/db/eligibilitydon your external startup disk. You’ll need administrator privileges to access and modify these files. - Backing Up the Original Files: Before making any edits, create a backup of the original files by copying them to a safe location. This step cannot be emphasized enough—any mistakes during this process could compromise your system’s integrity, and having a backup ensures you can restore normal functionality if needed.
-
Editing the Files: Open
eligibility_inputs.plistusing a plist editor such as Apple’s Xcode or any plain-text editor that supports XML. Look for the keyExternalBootDriveInputwithin the file. This typically contains an array of inputs related to external boot drives. Depending on the specific workaround, you may need to adjust or insert additional keys that indicate eligibility for Apple Intelligence on external drives. For example:- Set the value of
OS_ELIGIBILITY_CONTEXT_ELIGIBLE_DEVICE_LANGUAGEto"en-US". - Add a subkey named
OS_ELIGIBILITY_INPUT_DEVICE_AND_SIRI_LANGUAGE_MATCHwith a value oftrue.
These adjustments effectively update macOS to recognize the external drive as eligible for Apple Intelligence.
- Set the value of
-
Locking the Modified File: After making the changes, you’ll need to lock the file to prevent macOS from overwriting it during future operations. Right-click the
eligibility_inputs.plistfile, choose Get Info, and check the Locked box in the info window.
Once your edits are complete, the modified eligibility_inputs.plist file should allow eligibilityd to pass external drives as “eligible” for Apple Intelligence. But your job isn’t quite done yet. To ensure the changes apply, designate your external drive as the Startup Disk under System Settings, restart your Mac, and boot from the external drive.
After rebooting, head to System Settings > Apple Intelligence & Siri. You should now see the ability to toggle Apple Intelligence back on, despite using an external drive as your boot volume. It can feel immensely satisfying to not only overcome this hurdle but also to regain access to the smart features you rely on.
While this method has worked for many, be advised: proceed with caution. Even small missteps—like omitting a key-value pair or accidentally corrupting the file format—can lead to unwanted glitches or render your system inoperable. If you’re unfamiliar with plist files or XML structure, don’t hesitate to enlist the help of someone with the technical know-how. Likewise, ensure that you’ve fully backed up all critical data before making any changes to your macOS system files.
For those who prefer a simpler approach or are wary of diving into macOS’s internals, there are additional third-party utilities that attempt to streamline this process. We’ll delve into those tools in the next section, offering accessible alternatives for users seeking less hands-on solutions while still enabling Apple Intelligence on their external drives.
If modifying system files sounds intimidating, don’t worry—you’re not alone. Thankfully, some talented developers in the macOS community have created third-party tools and scripts to simplify this process. These tools can bypass the need for manual edits to system files, making it easier for users, particularly those without technical expertise, to enable Apple Intelligence on external drives. However, it’s essential to approach these solutions with caution and a clear understanding of the potential risks involved.
-
Kyle Ye’s Eligibility Tool: One of the more popular and accessible options, Kyle Ye’s tool automates the process of modifying eligibility settings. It utilizes Terminal commands to adjust the necessary permissions and configurations for enabling Apple Intelligence on external drives. To use this tool:
- Download the utility from its official repository or trusted community sources.
- Run the tool via macOS Terminal, following the instructions provided in its documentation.
- The script will handle edits to the
eligibility.plistandeligibility_inputs.plistfiles internally, ensuring a smoother user experience.
This tool is widely praised for its simplicity, but as with any third-party software, you should back up your system and evaluate its source’s credibility before proceeding.
- Plist Modification Automators: Some developers provide AppleScript-based tools specifically designed to locate and tweak plist files without requiring users to dive into directories or code. These tools often come with a GUI (Graphical User Interface), where you can toggle options or input desired values for eligibility settings. While these solutions are user-friendly, they should still be used with care. Always scan downloads for malware and verify tool authenticity through developer introductions or forum feedback.
- CrossCheck Scripts: Advanced users can find pre-written scripts shared on forums or GitHub that automate key plist modifications. These scripts often include built-in checks to ensure compatibility with your macOS version and external drive. Running these scripts typically involves copying them into Terminal and letting them execute the changes. Remember, even if scripts seem well-documented, they can carry risks. It’s a good idea to run them in a virtualized macOS environment or on a test volume first to minimize potential harm to your main system.
While third-party tools offer a streamlined process, they are not without risks. These tools alter macOS’s default behavior, which can sometimes lead to unexpected system instability or software conflicts. Moreover, Apple does not officially endorse such solutions, so updates to macOS could potentially nullify their effectiveness. For this reason, it’s wise to test these methods on a non-critical drive or system before applying them to a primary workflow setup.
Another concern with third-party tools is the lack of transparency for how they handle sensitive system files. Some tools may inadvertently expose your macOS installation to vulnerabilities if they modify permissions improperly or fail to secure the eligibility files post-edit. Here are some best practices to minimize risks when using third-party solutions:
- Download tools exclusively from verified repositories, such as GitHub profiles hosted directly by the developer.
- Read user reviews or community testimonials to confirm the tool’s legitimacy and success rates.
- Use antivirus software to scan the downloaded files before opening them on your system.
- Back up your external drive and any critical data on your internal macOS installation prior to running the tool.
- Test the solution on a secondary machine or a virtual macOS environment, if possible.
Another important tip: always update macOS with caution after applying these changes. Significant updates to macOS may overwrite your file modifications or render third-party scripts incompatible. Before applying system updates, check online forums to see if others have successfully maintained functionality with the new macOS release. If you’re using utilities like Kyle Ye’s tool, developers often post updates or patches for macOS adjustments, so keep an eye on their support channels.
For users who feel stuck or encounter challenges with any tools or scripts, macOS user communities—like those on Reddit, GitHub, and discourse forums—can be invaluable. Engaging with others who have successfully enabled Apple Intelligence on external drives allows you to learn from their experiences, troubleshoot issues, and discover less-publicized methods that could work for your specific setup.
Remember, enabling Apple Intelligence through third-party tools is not officially supported by Apple. The flexibility and enhanced functionality gained come with a degree of responsibility. By putting safety first—through backups, careful tool selection, and familiarity with the process—you can safely reclaim features like Apple Intelligence on your external boot drives and continue to benefit from macOS’s adaptability and power.
When undertaking any advanced modifications to macOS, especially those aimed at enabling Apple Intelligence when booting from an external drive, it’s essential to recognize the potential risks involved. Altering system files or using third-party tools can unlock desired functionality but can also introduce unexpected issues or vulnerabilities. Let’s break down the key risks to watch out for and the best practices to follow for a safer, more efficient process.
-
Risk of System Instability: Apple’s default system configurations exist for a reason—they are designed to ensure stability, security, and performance. Modifying system files like
eligibility.plistor using unsupported tools can disrupt these configurations, leading to unexpected crashes, system slowdowns, or unpredictable behavior. For example, editing plist files without understanding their structure might corrupt the file, making macOS unable to boot correctly. - Security Vulnerabilities: Disabling System Integrity Protection (SIP) or altering hidden system files can expose your Mac to potential threats, as the built-in safeguards designed to protect your operating system are intentionally loosened. If these changes fall into the wrong hands—e.g., malware exploiting modified file permissions—it could compromise your entire system.
- Loss of Functionality with Updates: Apple frequently updates macOS, and those updates might overwrite any changes you’ve made or render certain third-party tools incompatible. This means you could lose access to Apple Intelligence after investing time and effort into enabling it. Worse, attempting the same fixes post-update without compatibility patches might further destabilize your macOS installation.
- Data Loss: Incorrect modifications—or even successful changes that go wrong later—can lead to loss of access to critical data, especially if your external drive is your primary startup disk. This risk is heightened if you don’t maintain regular backups or if your changes affect disk permissions, making files unreadable or the drive unbootable.
- Unintended Consequences: It’s not uncommon for seemingly small system tweaks to produce cascading effects elsewhere in macOS. For instance, enabling Apple Intelligence might inadvertently interfere with other features, create conflicts with regularly synced Apple services (like iCloud), or even cause issues with new installations from the App Store.
While these risks might sound intimidating, there are proactive steps you can take to minimize their impact and enhance the safety and reliability of your setup. Here are some best practices to keep in mind:
-
Perform a Full Backup: Before making any changes to your macOS setup, use Time Machine or a trusted third-party backup tool to create a full backup of both your internal drive and your external startup disk. Additionally, save copies of the original
eligibility.plistand related files before editing them. A robust backup ensures you can restore your system to its original state if something goes wrong. - Test on a Non-Critical Setup: If possible, avoid making these changes on a production machine or your primary macOS environment. Create a test installation of macOS on another drive or partition and implement your modifications there first. Testing in a controlled environment allows you to troubleshoot and refine the process before applying it to your main system.
- Document Your Changes: Keep a record of every edit you make, including the specific files you modify, the keys you change, and the values you input. This documentation can be invaluable for troubleshooting or undoing changes later. Additionally, if a macOS update causes issues, you’ll have a clear reference to consult when applying adjustments after the update.
- Verify Tool Credibility: If you decide to use third-party solutions, do thorough research to ensure their legitimacy. Only download from reputable sources like GitHub or well-reviewed developer websites. Check if the tool’s repository has an active community or recent updates, as this indicates ongoing support for the software.
- Use Virtualization for Testing: Advanced users can replicate their macOS environment within a virtual machine. This allows changes to be tested in an isolated, low-risk setting. If an error occurs, the affected virtual system can be discarded without impacting your actual Mac.
- Keep SIP Enabled (if Possible): While some modifications may require disabling SIP, try to limit its deactivation to the bare minimum timeframe necessary. Once you complete your edits, re-enable SIP to restore your Mac’s full level of system security.
- Monitor Community Feedback: Stay connected to user forums, community groups, and online discussions surrounding Apple Intelligence modifications. These platforms can provide valuable insights, including solutions to common problems, compatibility updates, and early warnings for potential risks tied to future macOS updates.
Finally, always have an “escape plan” ready. Familiarize yourself with macOS’s recovery options, such as booting into Recovery Mode to reinstall macOS or using external recovery drives to restore backups. Being prepared to recover your system, no matter what, will give you the confidence to experiment without fear of irreversibly damaging your setup.
Remember, even though the appeal of enabling Apple Intelligence on an external drive is clear, these advanced steps may not be worth the risks for every user. Approach them thoughtfully, arm yourself with knowledge, and prioritize stability and security in your workflow. With the proper precautions, you can explore these capabilities while minimizing potential downsides.
