As technology continues to advance at breakneck speed, the capabilities of tools like GrayKey are nothing short of remarkable—yet also a bit unnerving. If you’re wondering exactly what this device can achieve, especially when you hear the term “iPhone hacking,” it’s understandable to feel a mix of fascination and concern. GrayKey, developed originally by Grayshift, is a law enforcement tool designed specifically to bypass the security protocols on Apple iPhones. Let’s break down what this powerful little box can actually do.
- Unlocking iPhones: GrayKey has the ability to unlock a variety of iPhone models, even those running the latest iOS versions. This means that security defenses like password attempts, Face ID, and Touch ID—which are put in place to protect your personal data—can all be bypassed. For investigators who are working tirelessly to solve crimes, unlocking an iPhone could be the key to accessing crucial evidence. On the other hand, if you’re someone who values privacy, this ability alone probably raises some red flags.
- Data Extraction: But unlocking a phone is just the beginning. Once it has access, GrayKey can extract a broad range of information from the device. Think about your own phone for a second—what’s on it? Text messages, call logs, photos, videos, browser history, and even app details can all be accessed. Data stored in apps like Snapchat, WhatsApp, or Instagram, which you might assume is somewhat protected, can become part of the extracted information. In a criminal investigation, this level of access could break the case wide open. But if a malicious actor got hold of this tool or if it was used without proper oversight, it’s not hard to see how dangerous that kind of access could become.
- Offline Operation: One compelling feature of GrayKey is its ability to function offline. So, law enforcement doesn’t need an internet connection to operate the device. From a tech perspective, it’s pretty impressive because it lowers the risk of that sensitive data being transferred over potentially insecure networks or compromised during the extraction process.
- Simple, User-Friendly Design: Despite its powerful capabilities, GrayKey isn’t just for tech geniuses or hackers. The device features a straightforward user interface, making it accessible for law enforcement agencies with varying degrees of technical expertise. This fact broadens its usability but might also bring up concerns about its potential deployment in less-than-ethical hands or situations.
- Supporting Different iPhone Models: Whether it’s an older iPhone model or a brand-new one, GrayKey adapts. It works with a wide range of iPhones, as well as different versions of iOS. This ongoing compatibility is part of what gives it that cat-and-mouse reputation—constantly adjusting and updating to keep up with Apple’s latest enhancements.
Of course, while GrayKey is an incredibly advanced and beneficial tool for law enforcement, its very design prompts as many questions as it answers. How is this technology being monitored? Who’s ensuring it’s only used in the right circumstances? And with iPhone security always evolving, how far behind can these devices fall when Apple pushes the next big update? That sort of tug-of-war between security enhancements and hacking tools continues to rage on, affecting not just those involved in law enforcement, but everyday users just like you.
In the modern world’s ever-evolving landscape of digital crime, law enforcement is under increasing pressure to keep up with criminals who use technology to conceal their actions. The harsh reality is that today’s most critical evidence often exists on smartphones—think about the last time you didn’t have your phone by your side. For law enforcement, devices like GrayKey can be a game-changer when it comes to accessing that evidence, but let’s be honest, it’s also understandable if such technology creates mixed feelings. After all, GrayKey’s ability to unlock and extract iPhone data is powerful, but it raises questions—about ethics, about privacy, and about how this tool is actually used in practice.
When first introduced in 2017, GrayKey mostly flew under the radar, aiding law enforcement agencies in a variety of contexts. Its principal function—unlocking iPhones—strikes at the core of many critical cases, from drug trafficking to national security matters. But what does this really look like in the field, and what kind of impact is GrayKey making in these investigations?
- Solving Crimes: Think of moments when the mere ability to access a suspect’s smartphone could drastically shift the direction of an investigation. In 2019, a pivotal murder case in the United States was unlocked—quite literally—through the use of GrayKey. Encrypted messages stored on the iPhone of a suspect were retrieved, revealing key communications tied to the crime. By breaking through the phone’s security, law enforcement was able to review conversations, location data, and timestamps, all of which fed into the eventual conviction. It’s cases like this where the tool’s abilities shine in service of justice.
- Tapping into Unseen Data: Beyond murder cases, GrayKey is often employed in investigations involving drug cartels and human traffickers. Organized crime is notorious for using encrypted communications platforms to fly under the radar of conventional surveillance tactics. But with GrayKey, law enforcement can retrieve not only text messages but also encrypted data stored on your favorite messaging apps like WhatsApp and Telegram—services that many criminals believe are impenetrable. And let’s not forget about tracking app data like location history to map out movements and bring fraudulent or dubious activities under scrutiny.
- Wider Intelligence Gathering: Even in cases that don’t immediately appear to be high-crime, like smaller fraud or burglary offenses, smartphones hold a wealth of untapped intelligence. Often, retrieving just one crucial piece of information—from a single call log to an unnoticed photo—can help agencies build wider intelligence surrounding an individual, their social circles, or larger operations. GrayKey is fast becoming a tool of choice in many of these less obvious cases because even what seems like the smallest digital footprint can blow investigations wide open.
But perhaps the elephant in the room is this: What safeguards are in place for when this kind of powerful tool is used on innocent people or in less clear-cut situations? For every legitimate use—like tracking down a trafficking network or identifying individuals in cybercrime rings—there’s concern about its potential for overreach. Without diligent oversight, technologies like GrayKey run the risk of being used too broadly, not only in major crime cases but possibly even minor or ambiguous legal battles. And for bystanders or people with no ties to suspected crimes who find their privacy exposed because of an unlocked phone, the situation blurs the line between investigation and intrusion.
That unpredictability in its use is what raises eyebrows, and it’s understandable if you’re feeling conflicted, especially given the tightrope walk between privacy rights and public safety. Official channels argue that stringent rules and warrants are in place to prevent this, ensuring GrayKey is used only when truly necessary. In theory, this means the tool is reserved for high-stakes cases where evidence retrieval could prove to be essential—cases that frequently involve victims of serious violence, child exploitation, and organized crime. But as we all know, theory and reality don’t always align perfectly.
Nonetheless, for law enforcement working within these guidelines, GrayKey’s role is clear. Its ability to effectively lend access to digital spaces that would otherwise remain locked can shorten investigation timelines, prevent further harm, and deliver the evidence needed for successful prosecutions. That’s no small feat in a world where criminals are becoming increasingly savvy, using every technological advantage they can to keep their activities hidden.
So where does that leave us? Regardless of where you stand on the privacy-public safety spectrum, hearing about GrayKey’s successes in fighting crime can’t help but offer some perspective. There’s no denying its utility in bringing people to justice, stopping crimes in progress, and pinpointing criminal networks. Yet, as more of our private lives end up locked away on our mobile devices, it’s hard not to consider how easily that key to unlocking crime could unlock our private lives too. The duality of that concern is something society will continue to wrestle with as GrayKey—and similar tools—become further embedded in law enforcement practices.
There’s no doubt that GrayKey’s capabilities have revolutionized law enforcement investigations. However, with this technological power comes significant responsibility, and unfortunately, it also raises a variety of ethical, legal, and privacy concerns that aren’t easy to ignore. If you’ve been feeling uneasy about what you’ve heard so far, you aren’t alone—many people share these concerns whether they’re privacy advocates or simply everyday users. After all, we’re not just talking about how law enforcement can use such a powerful tool; we’re also talking about potential misuse, overreach, and unintended consequences.
First and foremost, privacy is at the heart of the issue. It’s likely not hard to understand why people might feel uneasy about a device that could, in theory, expose all of the private data that we keep on our phones. If you’ve ever stored sensitive information (whether it’s your bank details, personal conversations with loved ones, or private photos), then imagining that information being extracted without your consent can be deeply troubling, regardless of whether you’re a law-abiding citizen. But more than that, this concern taps into a larger, more pervasive issue in today’s digital world—individuals feel they are losing control over who has access to their personal information.
This is where the ethical questions around the use of GrayKey start to arise. Is it always ethical to hack into a phone, even when a crime is suspected? What about situations where the phone of a person under investigation contains sensitive information not related to the crime at hand? These inquiries don’t have straightforward answers, and navigating this ethical gray zone is difficult—there’s a fine line between securing justice and infringing on individual rights.
One of the most talked-about controversies in this space is the issue of consent. Law enforcement agencies typically obtain a warrant before using GrayKey, but is this enough to protect individuals’ rights in every circumstance? Some argue that the rapid evolution of digital technologies like GrayKey requires us to rethink traditional legal frameworks. A search warrant for a phone is not quite the same as a warrant to search a home or a car. Mobile devices are a repository not just of personal effects but of far deeper insights into our personal lives, habits, and even emotional states. Given this, we need legal protections that reflect this reality, especially as hacking tools become more sophisticated.
Moreover, there are legitimate concerns about who gets access to these tools. Governments assert that tools like GrayKey are necessary and will only be used appropriately, but the lack of transparency surrounding when and how these devices are employed only fuels suspicion. What happens when such a tool ends up in the wrong hands? Could private firms or even malicious actors co-opt this technology, using it for aims far removed from justice? While law enforcement agencies stress that they employ strict oversight, the opacity surrounding GrayKey’s usage involves a significant trust leap—a leap not everyone is comfortable making.
Then there’s the ripple effect—how laws and access to such powerful devices like GrayKey influence global privacy rights and legal precedents. The playing field isn’t always equal across countries, and while one nation might impose strict limitations on tools of this nature, others could exploit them without the same degree of accountability. The fear, shared by many privacy advocates, is that the widespread availability of hacking tools and their use, even by official parties, might set a dangerous precedent for digital surveillance, effectively normalizing intrusive practices.
Not surprisingly, many have called for stronger safeguards and reforms. For advocates and even some policymakers, legislation protecting digital privacy needs to evolve to meet these emerging challenges. As of now, much of the legal landscape is still catching up to the advanced mechanisms behind hacking tools like GrayKey, and it’s not entirely clear how sustainable this reactive approach is. New laws and legal interpretations are essential to defining clear standards around law enforcement’s use of digital tools, ensuring a balance between security needs and personal freedoms.
In fact, privacy and the future legality of tools like GrayKey have become issues discussed on a global scale. The General Data Protection Regulation (GDPR) in Europe is illustrative of the growing push for comprehensive, people-centered privacy protections, with strict rules around data access and transparency enforced through heavy fines. Similar legal frameworks are now being debated in the U.S. and other parts of the world as awareness about digital rights has surged, in part because of stories about hacking tools like GrayKey making headlines.
Of course, one common response from law enforcement to these concerns is that tools like GrayKey are essential for tackling crime in a modern world where people, including criminals, are becoming more savvy in using encryption and security protocols to cover their tracks. Despite some flaws, no one can deny that tools like GrayKey help solve otherwise impenetrable cases involving human trafficking, terrorism, and violent crimes. And for many, this focus on public safety ought to weigh heavier on the scales of justice than the potential for abuse, especially if law enforcement is acting under legal constraints. Yet, privacy advocates push back—arguing that the innocent shouldn’t be asked to sacrifice their privacy, no matter the potential criminal incentives that might exist.
It’s here that you can see just how tricky the debate becomes. On one hand, the demand for public safety is evident—terrorism, organized crime, and cybercrimes are increasingly sophisticated and difficult to prosecute without these advancements. On the other hand, who will protect personal privacy from too much governmental—or technological—overreach? Are we sacrificing too much of our autonomy in the name of security? These are tough questions, and it’s clear that societies worldwide are struggling to find an answer.
So, where do we draw the line? It’s a question only time, further discussion, and potentially new laws will answer. But in the meantime, it’s natural to feel a bit uneasy and to question how your data might be subject to this ever-changing technological landscape.
The limitations of GrayKey reflect the broader, ongoing battle between technology providers like Apple and law enforcement-focused companies like Grayshift. It’s a type of digital arms race, where Apple tightens security with each iOS update, and in turn, companies like Grayshift work to circumvent these protections. If you’re feeling caught in the middle, you’re not alone—it’s a bit of a tug-of-war, with both sides rapidly evolving in a continuous pursuit to outsmart the other.
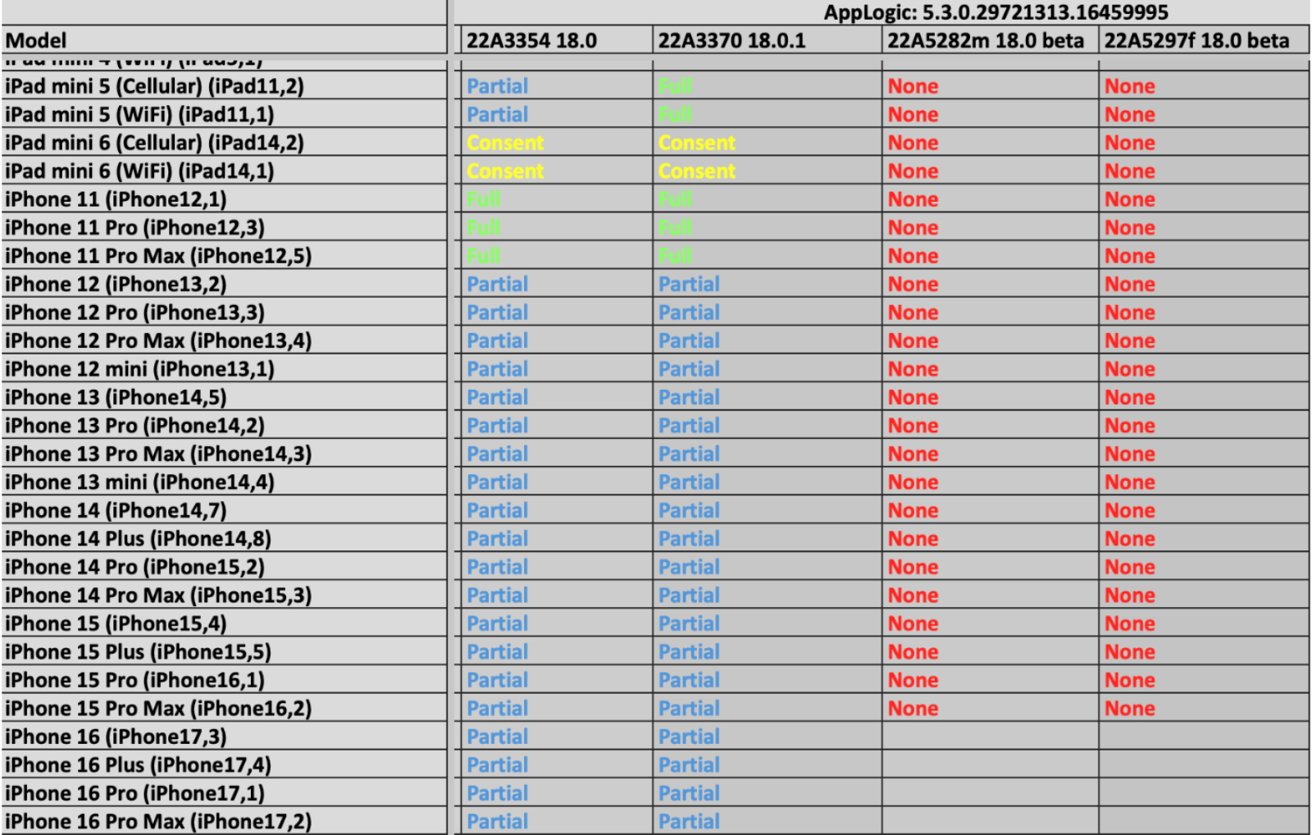
One major limitation that GrayKey faces is its performance with the most up-to-date iOS versions. Every time Apple releases a new software or OS update, it’s essentially trying to stay one step ahead of hacking tools like GrayKey, making their job more difficult. For example, leaked documents showed that iPhones running the newly released iOS 18 and iOS 18.1 posed significant challenges for the device. In these cases, only partial data extraction was possible, leaving some critical information out of reach for investigators. On iOS beta versions or phones that had specific security patches, GrayKey’s success rate dropped even further, at times failing to retrieve any data at all.
This constant back-and-forth can feel a bit like a cat-and-mouse game—Apple builds a new wall, and Grayshift figures out how to slowly chip away at it. Many of you might have experienced your own phones insisting on “important” security updates nearly every month. While those updates can feel incessant, they are, in part, Apple’s efforts to thwart tools like GrayKey. The reality is: there’s never really a finish line. Each new iOS update typically brings greater encryption and security enhancements, forcing companies like Grayshift to develop new methodologies and techniques just to keep up. Think of it as a high-stakes chess match, with both sides constantly evolving their strategies.
And it’s not only about iOS versions—it’s also the hardware itself. With every iPhone release, Apple incorporates better security features. Take the Secure Enclave, for example—Apple’s hardware-based key manager that makes it significantly harder for unauthorized parties to access sensitive data. As the Secure Enclave becomes more sophisticated, tools like GrayKey must also become more advanced to handle the challenge, increasing both the cost and complexity of such hacking attempts.
For law enforcement relying on GrayKey, this struggle to keep up can create a real bottleneck in investigations. Imagine gaining access to an iPhone that could hold all the answers to a criminal case, only to find out that GrayKey can’t fully extract the data due to an iOS update that went out a few days prior. It’s a frustrating situation, and agencies are often left waiting for tools like GrayKey to catch up to the latest security patches. This need for constant adaptation could delay critical breakthroughs in ongoing investigations, adding pressure to law enforcement teams.
Beyond iPhones, the situation becomes even more unpredictable when it comes to Android devices, which vary significantly across manufacturers, operating systems, and security standards. The fragmented nature of Android phones means that a tool like GrayKey may perform well on one model (perhaps a Google Pixel) but may struggle with another that has a completely different security architecture. For law enforcement, this inconsistency can be frustrating; what works seamlessly with one device may fall short with another, complicating investigations.
But this isn’t just a matter of performance—it also raises the question of how long GrayKey and similar tools will keep up with the increasingly sophisticated landscape of phone security. It’s not just Apple and Android pushing the envelope: everyday users are rapidly adopting more privacy features too, like encrypted messaging apps (Signal, WhatsApp, Telegram) and stronger, multi-factor authentication methods. This dynamic interaction of evolving personal habits and corporate innovations means law enforcement teams using GrayKey are likely to feel more challenges ahead.
Still, it’s important to remember that tools like GrayKey don’t operate in isolation, and part of its limitation stems from legal oversight too. Law enforcement’s ability to use these tools effectively depends heavily on obtaining the necessary legal permissions, such as warrants, and the integrity of existing laws to guide appropriate use. Without clear, up-to-date legal frameworks, agencies might find themselves not only technologically thwarted but legally constrained, adding to the time and complexity of any investigation.
As technology advances and cyberattacks grow more sophisticated, this dynamic of limitations versus adaptability will likely only escalate. But what’s clear is that both technology companies like Apple and investigative tools like GrayKey are locked in an endless race, with the stakes growing higher and the margin for error shrinking day by day. Navigating this intricate game will not only demand better tools but also more collaboration between law enforcement, tech companies, and lawmakers to ensure that both personal privacy and public safety are given due consideration.
